Phishing: Recognize and Report
Phishing is a type of email scam where the attacker sends emails that impersonate a company (often financial), a service desk, an employer, or someone that you already know and trust. The goal is to:
- steal personal information by tricking you into entering your username and password, PIN, or other sensitive information.
- install malware or viruses on your computer that can record keystrokes, capture saved or stored information, or destroy files.
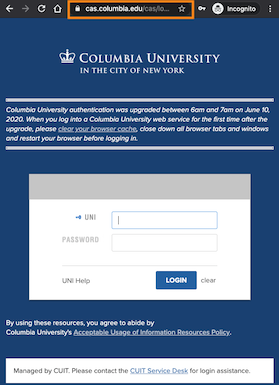
For example, Columbia students, faculty and staff may receive emails that appear to come from trusted sources like "CUIT Service Desk," "MyColumbia," or "President Bollinger," with a link to a website where you are asked to enter your username and password to "verify your account" (see "How to spot a fake Columbia CAS login page," below.)
How to Handle a Phishing Message:
1. Identify the email as suspicious.
Phishing messages usually have one or more of the following:
- Spelling or grammatical errors. These should be immediate red flags.
- Heightened urgency. Phishing attempts often try to get you to respond before you have a chance to think.
- Generic signatures. A signature line with "Service Desk" or "Administration" rather than a University official whose name you can verify.
- Requests for personal information. A request for personal information from contacts you did not initiate.
2. If you think it's suspicious, report it:
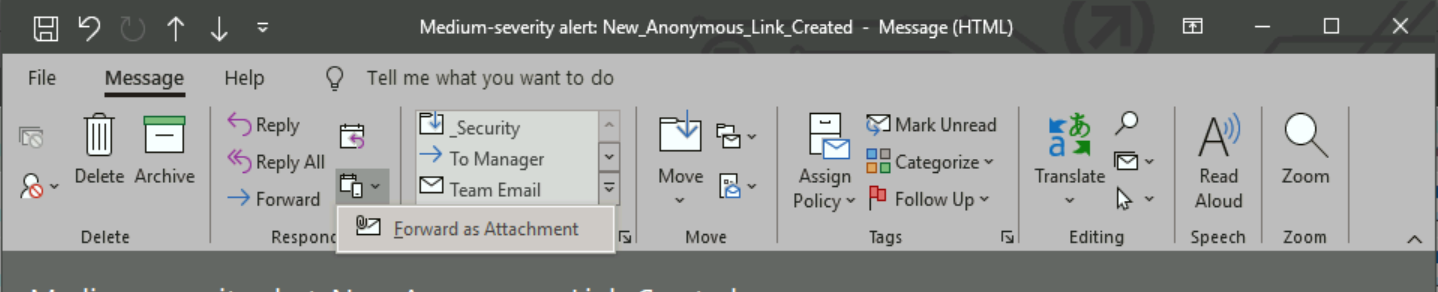
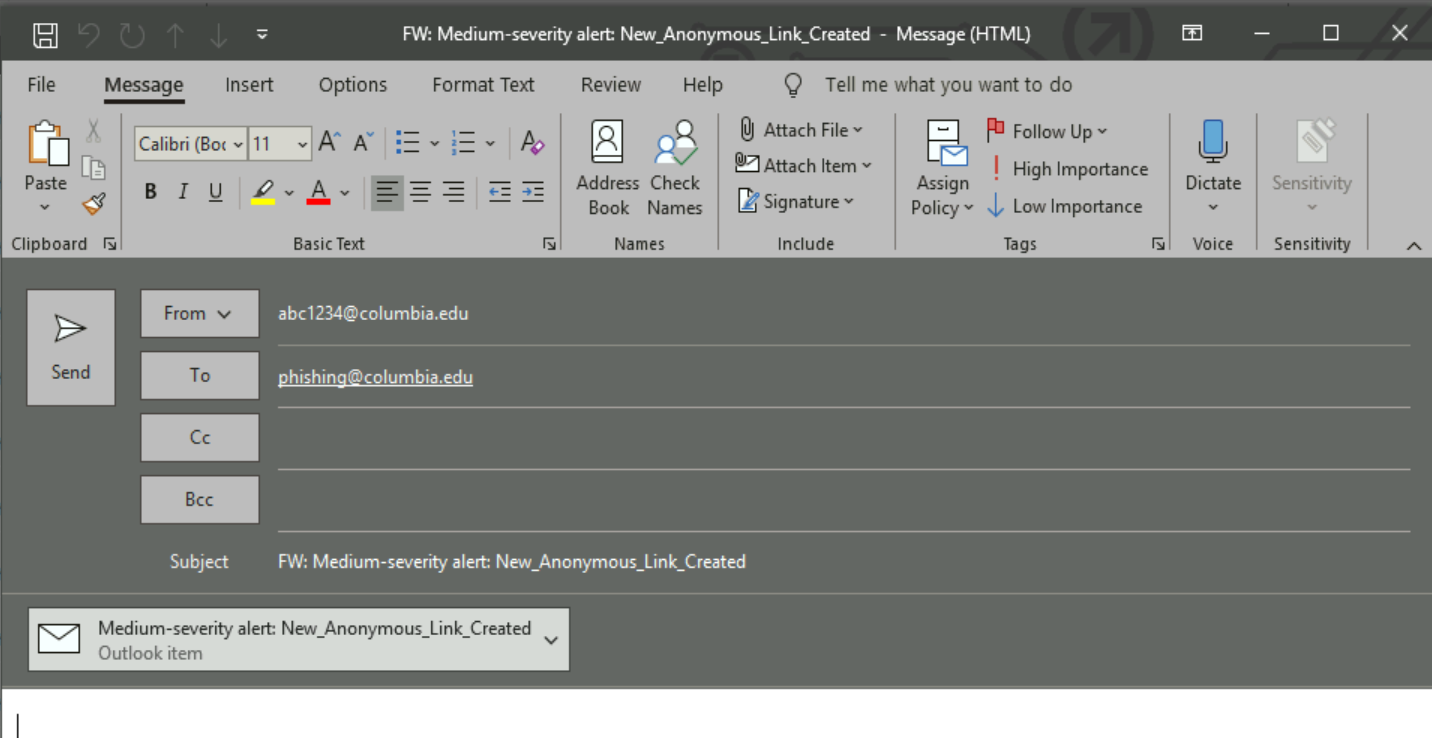
- Report the email to [email protected] with full headers (see "How to report a suspicious email to [email protected]," below) so the CUIT Cybersecurity team can investigate.
- CUIMC Users: If the suspicious email was sent to a @cumc.columbia.edu email address, please send the phishing attempt with full headers to [email protected].
- If in doubt, contact the CUIT Service Desk at 212-854-1919. (CUIMC Users: 212-305-4357, option 5.)
3. If you already clicked on a phishing link or have entered your information on a suspicious site:
- Change your password at Manage My UNI immediately. (CUIMC Users should update with myPassword).
- Contact the CUIT Service Desk at 212-854-1919. CUIMC Users: 212-305-4357, option 5.)